What is Windows Event Log ID 4740? – A User Account Was Locked Out. Well, if you are an IT professional, you might have come across a situation where a user account gets locked out on your Windows Server. This is due to multiple reasons, such as entering the wrong password multiple times or a security policy. Hence, in such cases, it becomes essential to identify the root cause of the lockout and take necessary action to prevent it from happening again.
Consequently, to identify the cause of a locked out user account, use the Windows Event Viewer. This article discusses Windows Event Log ID 4740, which indicates that a user account was locked out.
What is Windows Event Log ID 4740?
All in all, Windows Event Log ID 4740 is a security audit event logged in the Windows Event Viewer when a user account gets locked out. Furthermore, this event is generated on domain controllers and provides valuable information to help IT professionals troubleshoot account lockout issues.
Well, whenever a user account is locked out Windows Event Log ID 4740 is logged with the following details:
• Event ID: 4740.
• Category: Account Management.
• Subcategory: User Account Management.
• Message: A user account was locked out.
By viewing the security logs in the Event Viewer and filtering for Event ID 4740, IT professionals identify the source of the lockout, such as the device or network address that was used for the failed login attempts.
Further, once the source of the lockout is identified, IT professionals take necessary action to prevent it from happening again, such as resetting the user account password, checking for scheduled tasks or services running under the user account, or verifying if the user has saved their password on a public computer.
How to view Windows Event Log ID 4740?
Basically, in order to view Windows Event Log ID 4740, you follow these steps:
1. Open the Event Viewer:
- Press the Windows key + R on your keyboard to open the Run dialog box.
- Type “eventvwr.msc” in the box and click OK.
2. Navigate to the Security log:
- In the Event Viewer, expand Windows Logs in the left pane.
- Click on Security.
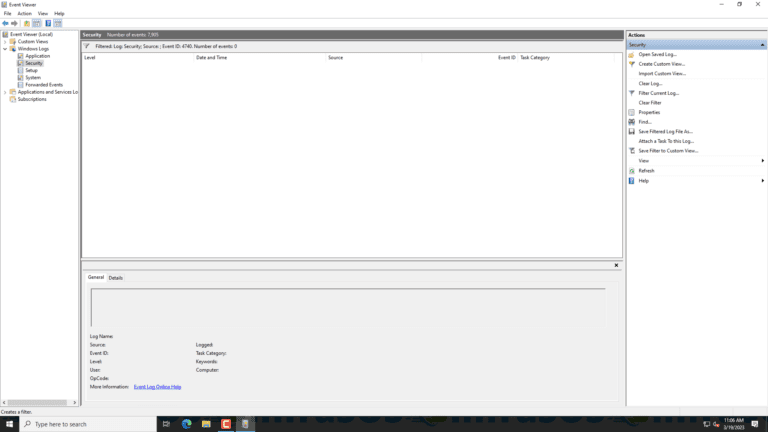
3. Filter the log for Event ID 4740:
- In the Security log, click on “Filter Current Log…” in the right pane.
- In the “Filter Current Log” window, type “4740” in the “All Event IDs” field.
- Click OK to apply the filter.
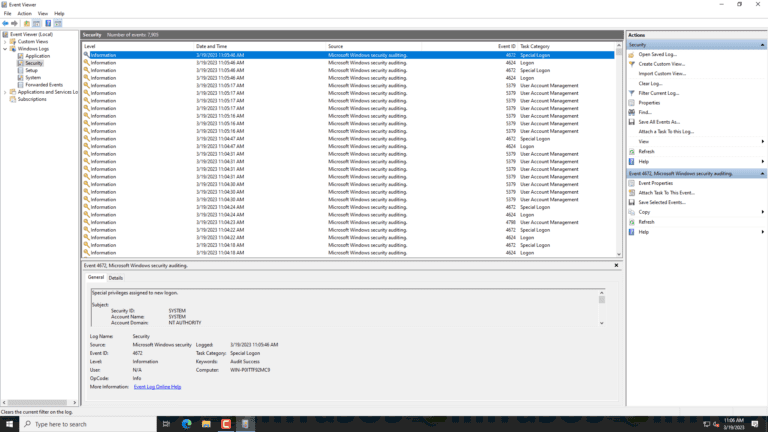
4. View Event ID Logs
- The Security log now show only the logs with Event ID 4740 logs.
- Click on any log entry to view the details, such as the time and date of the lockout, the user account name, and the source network address or device that caused the lockout.
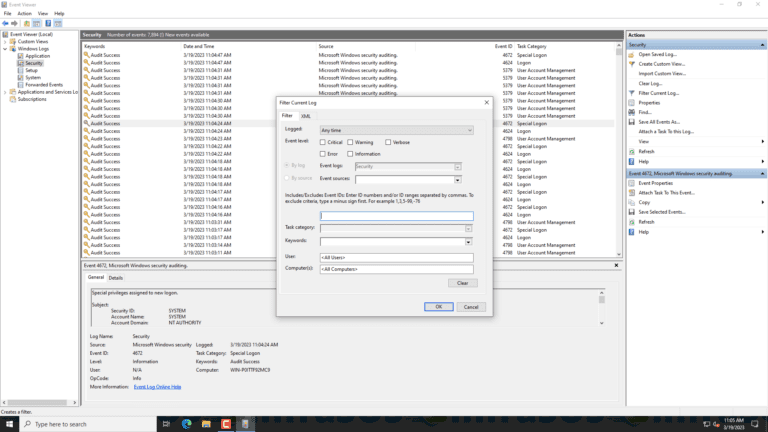
Note: If you are not able to view Event ID 4740 logs, it may be because the auditing of account management events is not enabled on the Windows Server. Enable it by following these steps:
Enable Audit Logs -Steps
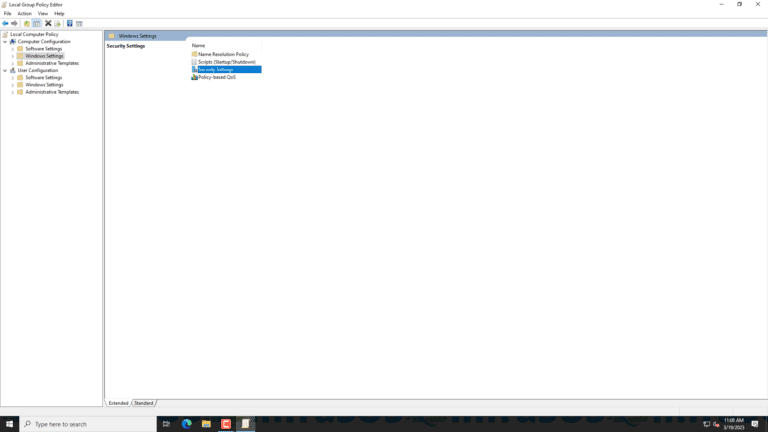
- Open the Group Policy Editor:
- Press the Windows key + R on your keyboard to open the Run dialog box.
- Type “gpedit.msc” in the box and click OK.
2. Enable auditing of account management events:
- In the Group Policy Editor, navigate to Computer Configuration > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies > Account Management.
- Enable “Audit User Account Management” and “Audit Computer Account Management“.
- Click OK.
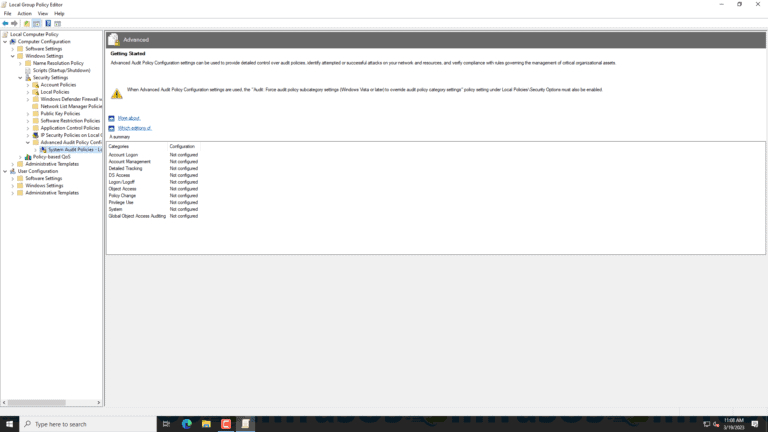
After the auditing of account management events is enabled, Windows Event Log ID 4740 logs are generated whenever a user account is locked out.
How to troubleshoot Active Directory locked out user account?
Specifically, when a user account gets locked out, it is frustrating for the user and causes productivity loss for the organization. Therefore, below are the possible solutions to troubleshoot a locked out user account:
Perform the Checklist below:
1. Check for simple causes:
- Make sure the user has entered their password correctly and not made any typos.
- Ensure that the user is not currently logged into another device or session.
2. View and check Event Viewer Logs:
- Follow the steps mentioned in the previous question to view Windows Event Log ID 4740 logs.
- Identify the source of the lockout, such as the device or network address that was used for the failed login attempts.
- If the source is a device that the user has previously used, make sure the device is not still logged in with the user’s credentials.
3. Reset the User Account Password:
- Remember, if the user has forgotten their password, reset the password and inform them of the new password.
- Ensure that the password meets the organization’s password policies and is secure.
4. Perform a check for scheduled tasks and services:
- Anyhow, if the user has scheduled tasks or services running under their account, these tasks could be causing the account to get locked out.
- Check the Task Scheduler and Services consoles for any tasks or services that are running under the user’s account.
- Update the credentials used for these tasks or services to prevent lockouts.
5. Check for saved credentials:
- If the user has saved their password on a public computer, such as a kiosk or shared workstation, the password could be getting used by someone else, causing the account to get locked out.
- Advise the user not to save their password on public computers and clear any saved credentials from the Credential Manager.
6. Perform a check for mobile device synchronization:
- But, if the user has synchronized their account with a mobile device, such as a smartphone or tablet, the device is potentially causing the account to get locked out.
- Ask the user to check their mobile device settings and ensure that they are using the correct username and password.
7. Contact the IT helpdesk:
- Above all, if the above solutions do not resolve the issue, contact the IT helpdesk for further assistance.
- The helpdesk analyse the account lockout issue and provide a resolution based on the organization’s policies and procedures.
What is Windows Event Log ID 4740? – A User Account Was Locked Out Conclusion
In this article, we discussed Windows Event Log ID 4740, which indicates that a user account was locked out. Moreover, we talked about how to view Windows Event Log ID 4740 and troubleshoot a locked-out user account. Finally, by following the steps mentioned in this article, you identify the source of the lockout and take necessary action to prevent it from happening again.